Cyber Security Management System
Cyber security management system. Cybersecurity management comprises a wide swath of different systems and applications that help to protect your digital identity maintain access management and enhance overall digital safety. About Cyber Management System Project. Systems Management and Cybersecurity CAREER CHOICES YOU WILL LEARN COURSE DESCRIPTIONS ADMISSION REQUIREMENTS Systems Management and Cybersecurity I think computer viruses should count as life.
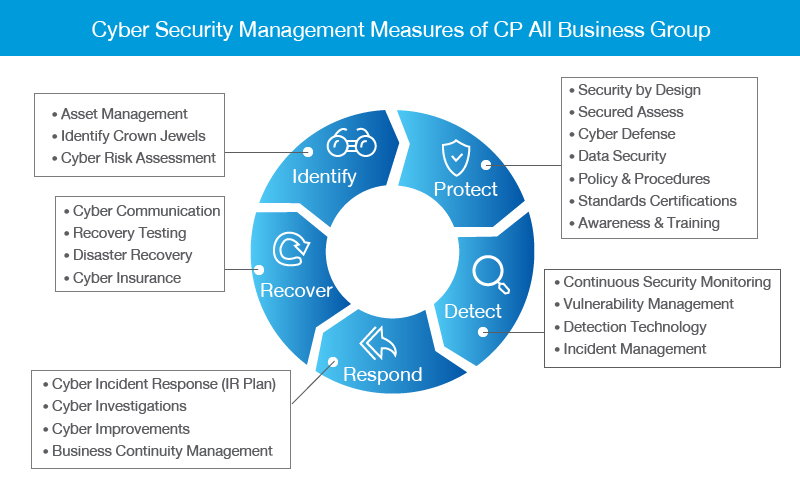
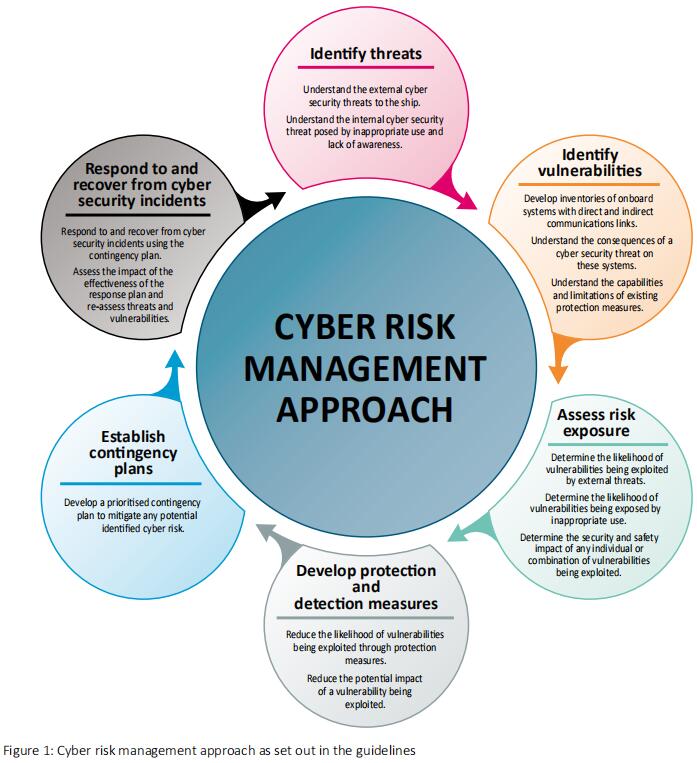
Appoint a person with overall responsibility Identify the risks in your organisation Mitigate those risks with security solutions Issue cyber security policies based on your risks Train your staff on your risks and policies and then test their awareness. Such a framework is not firmly associated with any particular cybersecurity standard and can be adapted during implementation to address any specific security standard that organizations using it wishes to follow. The Guidelines on Cyber Security Onboard Ships are aligned with IMO resolution MSC42898 and IMOs guidelines and provide practical recommendations on maritime cyber risk management.
I think it says something about human nature that the. You can define distribute enforce and audit security policies for multiple security devices from a central location. The server module or program is responsible for the management of settings and client request.
By contrast Tufin Orchestration Suite rates 435 stars with 14 reviews. WASHINGTON Today the Department of Homeland Security DHS launched the Cybersecurity Talent Management System CTMS a new personnel system that will enable DHS to more effectively recruit develop and retain our Nations top cybersecurity professionals. Acronis Cyber Protect is the unique AI-enhanced integration of Data Protection with Cybersecurity in a single service provider solution Acronis Cyber Protect Cloud is the single service provider solution that combines backup anti-malware security and management capabilities such as vulnerability assessments patch management URL filtering and more.
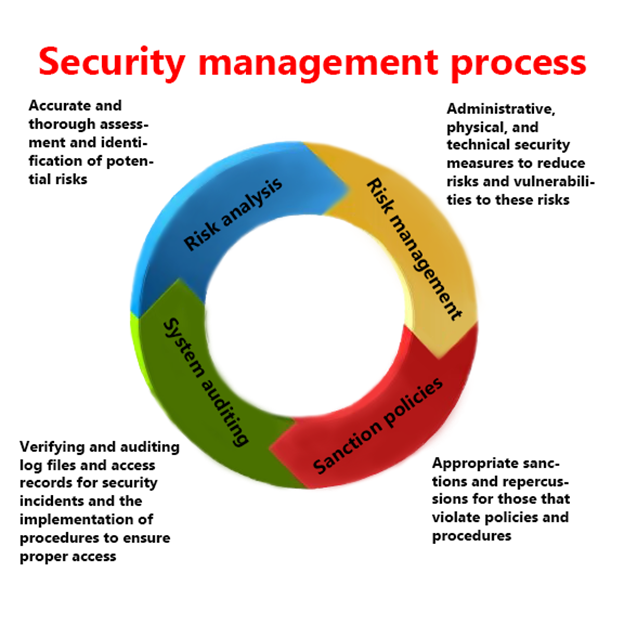
The cyber security management process is a known system of interrelated elements that act in concert with one another to achieve the over-arching goal of the system itself -- to protect the confidentiality integrity and availability of information. Client module and server module. R8030 Cyber Security Management rates 475 stars with 7 reviews.
Communications Security COMSEC Manager. Cybersecurity should be integrated into the overall risk management process of every government organization eg jurisdiction department or agency. Individual who manages the Communications Security COMSEC resources of an organization CNSSI 4009 or key custodian for a Crypto Key Management System CKMS.
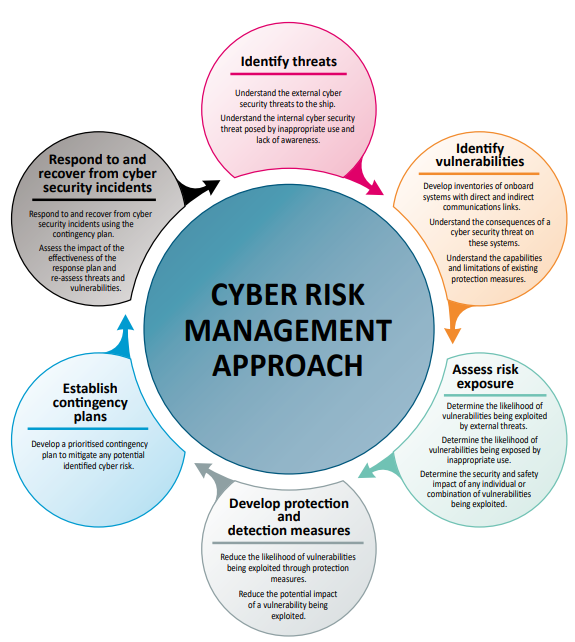
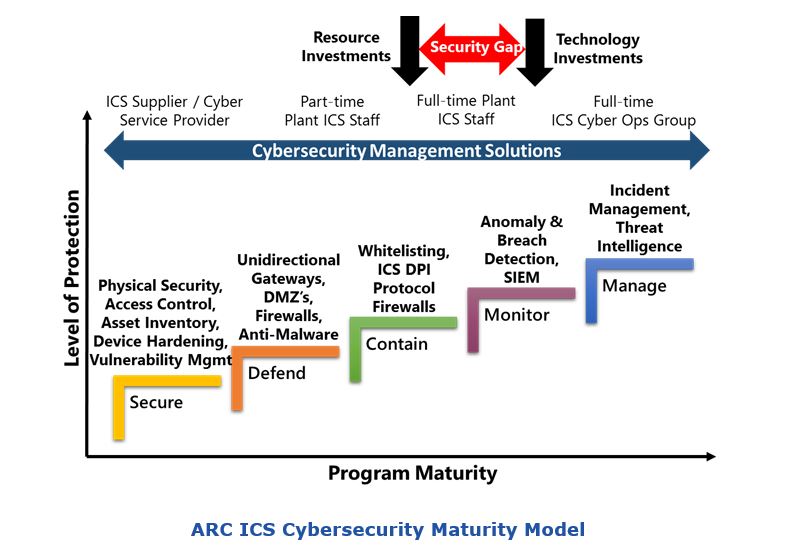
There are 5 steps. Because the purpose of cybersecurity is to support and protect business functions it must be aligned with business objectives and appropriately funded to match risks.
The number of cyberattacks is not expected to decrease in the near future.
The Cisco Secure Policy Manager formerly called Cisco Security Manager is a comprehensive security management system for Cisco Secure products. Cybersecurity management framework to address all countries industries and states. Individual who manages the Communications Security COMSEC resources of an organization CNSSI 4009 or key custodian for a Crypto Key Management System CKMS. CTMS will enable DHS to fill mission-critical cybersecurity positions by screening. Such a framework is not firmly associated with any particular cybersecurity standard and can be adapted during implementation to address any specific security standard that organizations using it wishes to follow. There are 5 steps. This paper introduces a. Moreover increased entry points for attacks such as with the arrival of the internet of things increase the need to secure networks and devices. Communications Security COMSEC Manager.
The system is divided into two modules. By contrast Tufin Orchestration Suite rates 435 stars with 14 reviews. The Guidelines on Cyber Security Onboard Ships are aligned with IMO resolution MSC42898 and IMOs guidelines and provide practical recommendations on maritime cyber risk management. The security management system is a very broad area that generally includes everything from the supervision of security guards at malls and museums to the installation of high-tech security management systems that are generally made to. With the ever-growing reliance on technology and interconnectivity its no surprise that theres an acute focus on cybersecurity and systems protection. Client module and server module. Security Management System ISMS is defined as an efficient method for managing sensitive company information so that it remains secure.


































Post a Comment for "Cyber Security Management System"